Xaccess Endpoint app
Xaccess Endpoint app is the client app that end users (Remote or Local) use to connect to the enterprise applications in the Xaccess private network. The app is installed on the user assets when Xshield agents (Type = User Access) are installed. The Endpoint app on the asset is tuned to grant secure access to applications over an IPsec connection with 256-bit key AES encryption on Windows 7 and Windows 8 OSes and 128-bit key AES-GCM encryption for all other supported OSes for Xaccess. S
User authentication
Xaccess supports building the user directory (in Xshield) using user identities fetched from Security Assertion Markup Language (SAML) IdPs and Active Directory (AD). You can also add Local users from the Xshield UI. Currently, you can use one of three supported methods to build the user directory - SAML IdPs, AD, or Local users.
For instances using multiple methods, for example, Azure AD and AD, the authentication mode is set to SAML. The precedence order for authentication with Xaccess is SAML, AD, and lastly, Local user authentication. For example, on an instance using Azure AD and Local users, you have to disable the SAML IdP integration to allow Local users to authenticate and join the Xaccess private network.
First login behavior
At first login with the Xaccess Endpoint app, the following is the expected behavior:
-
For Xshield instances that use a single IdP or AD for the user directory, the users are logged in at the first authenticated attempt.
-
For Xshield instances that use multiple IdPs ('n' number of) for the user directory, the users may be prompted for a maximum of ‘n’ authentication attempts. After a successful first login, they are logged in at the first authenticated attempt.
Log in to the Endpoint app
The Xaccess Endpoint app is located in the System Tray of a user asset.
-
Open the System Tray and right-click the ColorTokens icon (Red in color).
-
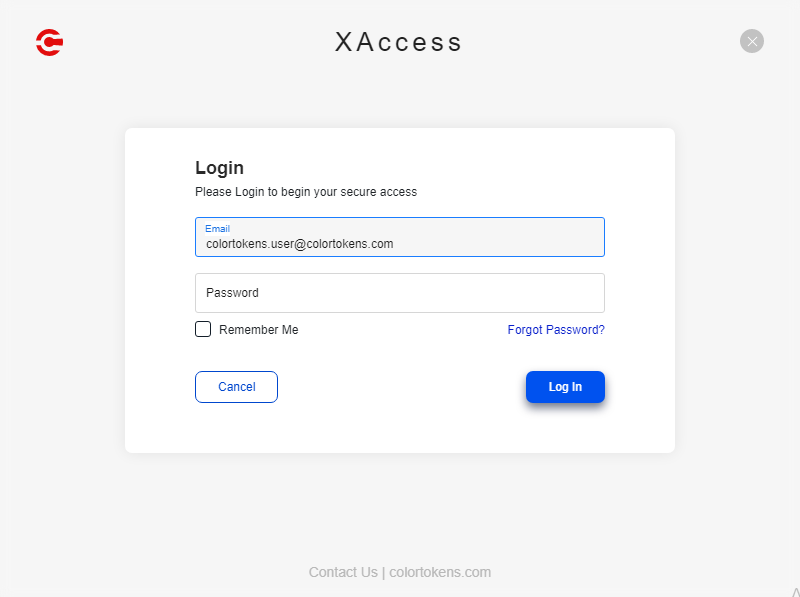
In the Email text box, enter the email address used to log in.
-
Click Continue.
-
In the Password text box, enter the password.
-
Click Log In.
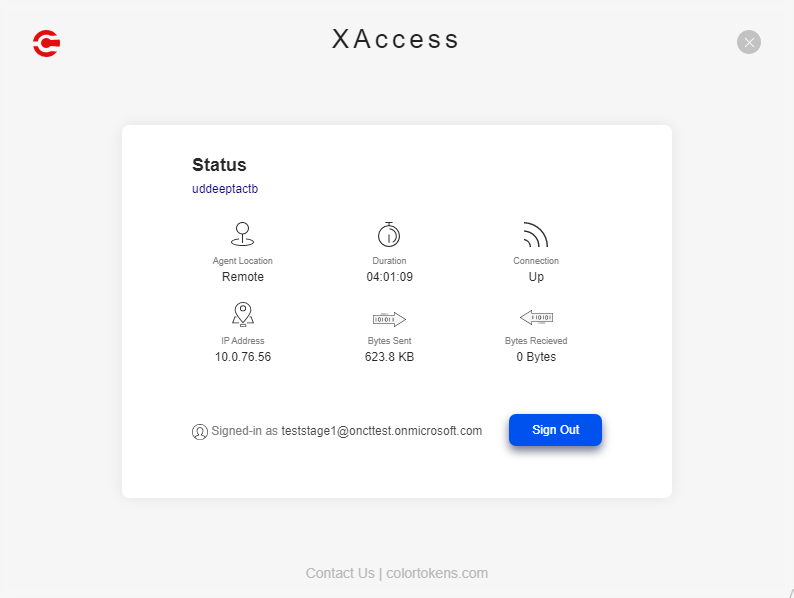
Successful login
|
After a successful login (first or subsequent), remote users are connected to the nearest CT Broker. All data exchanges with the protected applications happen over the IPsec tunnel. The CT Broker cluster routes remote user requests to applications to the appropriate CT Connectors. Users stay logged in with uninterrupted access to the applications. |
App settings
Remember meAD users and Local users can save their Xaccess login credentials after the first login to avoid entering them during subsequent logins.
Users from IdPs must use the IdP-native features (such as Stay signed in for Azure AD) to save their credentials. Reset passwordCurrently, Xaccess is not built to reset passwords from the Xaccess login interface and/or work with the Multi-Factor Authentication (MFA)features natively configured in the SAML IdP. Password resets must be initiated and completed using the native IdP or AD features. |
Log out of the Endpoint app
Users are automatically logged out of the Endpoint app if they are idle for more than the Session Idle Time duration set for the instance on the Xaccess > Settings > Advanced Configuration Settings page.
To log out of the app manually:
-
In the Xaccess pop-up, click Sign Out.
Common issues
Here are some of the common issues users may face when using the Xaccess Endpoint app to access the applications.
Users are unable to log in
| Cause | Solution | |
|
1 |
Incorrect/wrong username or password |
Enter the correct username and/or password. |
|
2 |
User account locked out because it exceeded the maximum number of attempts to log in with the correct username and password. |
Initiate and complete the password reset using the IdP-native password reset and/or MFA options. |
Remote users cannot access the usual applications/portals
| Cause | Solution | |
|
1 |
The user asset is quarantined with Xaccess Auto-quarantine policies. Either the firewall is turned OFF, or the OS has not been updated recently. |
Xaccess Quarantine template is an Auto-Quarantine template with a set of auto-quarantine conditions to check the device posture of the user assets. If the device posture is found vulnerable, the assets are quarantined. Quarantined assets can only access the emergency-access domains and subnets listed for the Endpoint group in which they are grouped in Xshield.
To regain access to the applications in the private network, the asset must be recovered to a healthy state using the OS-native procedures. |
| 2
|
Misconfigured policies |
For Remote users, the access is controlled by the relevant policies from the CT Brokers for the Xaccess private network.
|