Use Policy Builder to create policies
Use Xshield's Policy Builder to build policies between managed groups. You can use Policy Builder to build policies for all types of groups created and managed from Xshield - Workload groups, Network groups, Domain groups, and Endpoint groups. Policy Builder can considerably cut down the time needed to build Xshield policies.
Policy Builder can help you build policies that are Xshield group-centric. With Policy Builder, you select a managed group for which you want to build policies and build policies for that group with other applicable managed groups. You can build policies based on Observed traffic and custom or predefined Access parameters. For example, to create policies between a Domain group with Windows OS update domains and Workload groups with Windows assets, select the Domain group in Policy Builder and accept recommendations and/or add Access parameters between the groups.
With Policy Builder, the group you select initially is always the group to add policies. After you select a group, the selected group must either be the source or the destination for the policies.
Upon selecting a group, you will see the features to build policies for the group. Some of these features are available for all types of groups (group-independent features). You will see that some of the features are group-specific. For example, both inbound and outbound policies can be added only for Workload groups. Also, some of the features of Policy Builder are view-specific (only available in Visual or Tabular view). See Group views for more details.
Group views
With Policy Builder, you can build policies in two views - Visual and Tabular.
Tabular view
In the Tabular view, you can see the following:
|
Visual view
In the Visual view, you can see the following:
|
In the Visual view, you will not see the following Policy Builder features:
-
Policy recommendations and option to download all policies (recommended and assigned/enforced)
-
Key indicators of the selected group
-
Options to change the enforcement status of the group (if a Workload group is selected).
Toggle views
You can toggle between the views at any point in time when you are using Policy Builder.
-
To toggle, click the view icon located at the top-right corner.
Key indicators
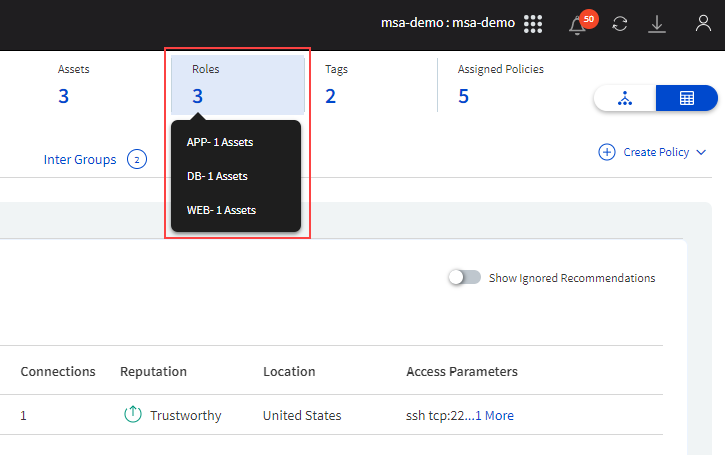
You will see some key indicators of the group you select to build policies at the top of the Policy Builder page. These vary by the type of group. For example, for a Workload group, the number of workloads/assets in the group, roles of the workloads, tags on the workloads, and policies assigned/enforced.
| Type | Key indicators |
|
Workload group |
Number of workloads/assets in the group, roles of the workloads, tags on the workloads, and policies assigned/enforced on the group |
|
Network group |
Number of IP address ranges, subnets, and policies assigned/enforced on the group |
|
Domain group |
Number of domains and policies assigned/enforced on the group |
|
Policy recommendations (in Tabular view only)
In the Tabular view of Policy Builder, Policy recommendations is a summary of traffic sessions between a selected group and other applicable Xshield groups. The details of the recommendation vary by the type of group. For example, for recommendations between Workload groups and Domain groups, you will see Threat reputation, Category, and the origin of traffic for the domain.
Recommendation categories
Policy recommendations for a group are categorized by the type of group with which the traffic is seen.
| Type | Categories/Tabs |
|
Workload group |
Public Networks & Domains, Private Networks, Endpoint groups, Inter Group, and Intra Group |
|
Network group |
Endpoint Groups and Workload Groups |
|
Domain group |
Endpoint Groups and Workload Groups |
|
Endpoint group |
Public Networks & Domains, Private Networks, and Workload Groups |
Act on recommendations
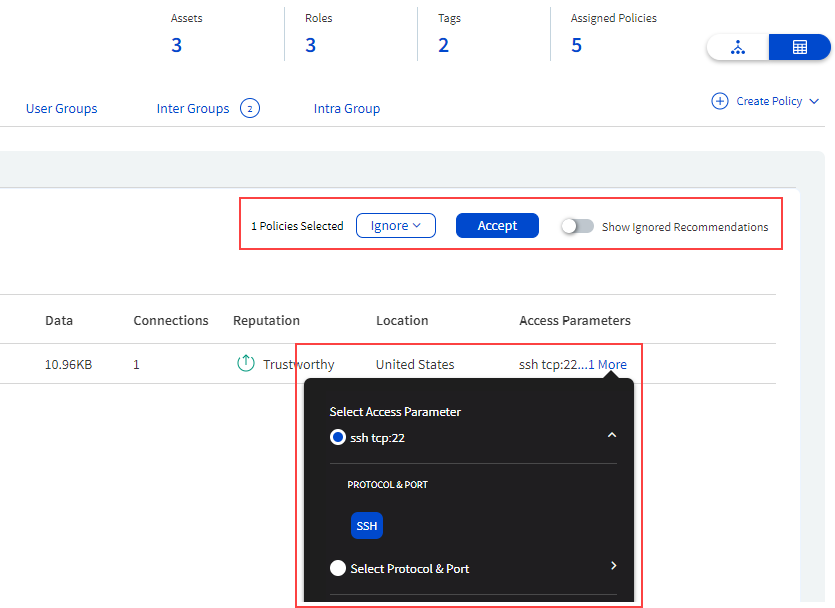
You can perform the following actions for recommended policies:
|
Add policies between groups
You can add inbound and outbound policies (depending on the group you select) by accepting the policy recommendations and using Access parameters between the source and destination groups.
-
To add policies, go to the relevant tab for the group, click Create Policy (located at the top-right corner) to add policies using the Access policies feature in Xshield. See Access policies for more details.
For Workload groups, you will see the following features to add policies.
Inbound and outbound policy recommendations and policies
You can add inbound and/or outbound policies between Workload groups and Network groups and Workload groups and Domain groups.
In Policy Builder, the policy recommendations and assigned/enforced policies for Workload groups are classified as follows:
-
Public Networks & Domains - these are related to the public and managed Network groups and Domain groups
-
Private Networks - these are related to the private and managed Network groups.
-
User Groups - these are policy recommendations for inbound traffic from Endpoint groups.
-
Inter Group - these are recommendations and policies between the selected Workload group and other managed Workload groups
-
Intra Group - these are recommendations and policies for traffic between the assets in the selected Workload group.
To add policies, accept policy recommendations, or add custom policies.
-
To add policies by accepting recommendations, go to the relevant tab, click Inbound or Outbound (if applicable), select a recommendation, and click Apply.
-
To add custom policies, go to the relevant tab, click Create policy, click Inbound or Outbound, and add policies using the Access policies feature in Xshield. See Access policies for more.
Change policy enforcement status
-
Click the 3-dot menu (located at the top-right corner) to change the policy enforcement to One of the following - Observe, Enforce and Encrypt.
Add policies by assigning Security policy templates and role-based policies
Because of its role/tier-based policy enforcement capabilities, Security policy templates are only applicable for Workload groups. Also, you can assign role-based Access policies between Workload groups and other managed groups and between assets in the selected Workload group.
-
To assign Security policy templates, go to the Intra Group tab, click Assign SPT (located at the top-right corner), and assign one or more Security policy templates.
For example, allow role-specific traffic between the workloads based on their roles in the Workload group.
-
To assign Access policies, go to the relevant tab, click Create policy (located at the top-right corner), click Inbound or Outbound, and add Access policies. See Access policies for more.
For example, create a data ingestion pipeline between the DB workloads in the source and destination Workload groups.
For other managed groups, you will see the following when you add policies.
-
For Network groups, the selected Network group is always the destination group for policies with Endpoint groups.
-
For Domain groups, the selected Domain group is always the destination group for the policies with Workload groups. However, in a Workload-centric approach, policy recommendations between Workload groups and Domain groups are shown both for inbound and outbound traffic from Workload groups.
-
For Endpoint groups, the selected Endpoint group is always the source group for the policies with Workload groups and Network groups.