Access policies
Access policies enforce rules that control how Workload groups, Network groups, Domain groups, and Endpoint groups communicate. In Xshield, a set of groups that are protected are 'Destination' groups, and the groups that access the protected groups are the 'Source' groups.
An Access policy is a set of inbound and outbound Access parameters enforced on the assets in the Source and Destination groups. In Xshield, an Access parameter is a named combination of port/port range and the protocol used on them. Ports and protocols that are not part of an Access policy are blocked on the assets in the Source and Destination groups.
In Xshield, Access policies can be enforced for the following combinations of Source groups and Destination groups.
| Source
|
Destination | Purpose |
| Domain groups | Workload groups
|
Enable continued software update and patch management for workloads
|
| Network groups |
Workload groups |
Enable access to infrastructure services
|
| Workload groups | Endpoint groups, Network groups, Workload groups
|
Enable access to Workload groups and for intra-workload group communication
|
Types of Access policies
Two kinds of Access policies exist in Xshield:
-
System-generated - these are Access policies that Xshield automatically creates when you enforce Corporate policy templates and Security policy templates to Workload groups.
System-generated Access policies cannot be edited or deleted. They change when you edit the related Corporate policy template or Security policy template or apply policy recommendations to Workload groups. They are not seen when you stop enforcing Corporate policy templates or Security policy templates.
-
User-created - these are Access policies you create to enforce access rules between groups.
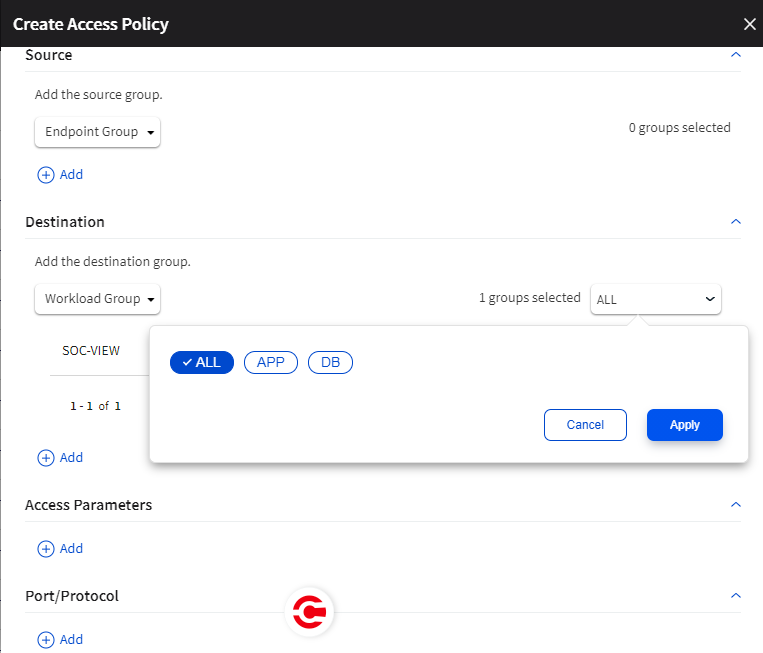
Create Access policy
Create multiple Access policies between different source and destination groups to protect critical groups in your network.
When a Workload group is used in an Access policy, you can assign the Access policy to all roles or a specific role (Web, App, or DB) in the Workload group. For example, with an Endpoint group as the Source, you can allow access only to the assets with the Web role in the Destination Workload group.
|
Enforce Access policies
-
If the Workload group associated with an Access policy is in the Enforced or Encrypted mode, the new Access policy is automatically enforced.
-
If the Workload group associated with an Access policy is in the Observed mode, the new Access policy is enforced only after the Workload group is moved to the Enforced mode.
When policies are successfully enforced on the assets in the Source and Destination groups assets, the related inbound and outbound Access parameters are added to the assets' native firewall.
Filter Access policies
When you create many Access policies, it may be hard to find Access policies you want to review or edit.
To filter the Access Policies page, search by the name of the Source group (Source group column) or Destination group (Destination group column).
Next steps
-
Enforce Access policies on the Workload groups to protect the Workloads.
-
Verify if the policies are pushed to the assets.
-
Monitor policy violation alerts related to Access policies between Source groups and Destination groups. Read Investigate alerts for more.
Investigate traffic flows between Source groups and Destination groups. See Investigate traffic flows for more details.