Interpret traffic flows downloaded from Flow Explorer
The CSV files you download from Flow Explorer contain the traffic flows/unique sessions between the Xshield-managed assets and other private and public unmanaged entities that communicate with the assets. You can build and strengthen Policies by analyzing the sessions in the CSV files. Use Microsoft Excel and other similar tools to filter the sessions by session IDs, 5-tuples, Policy action, and so on.
Here are a couple of things you must consider when you interpret the CSV files that you download from Flow Explorer (or from the Workload groups' fly panel).
a. Microsoft Excel's limitation with displaying more than 15 digits in a cell with the default settings
|
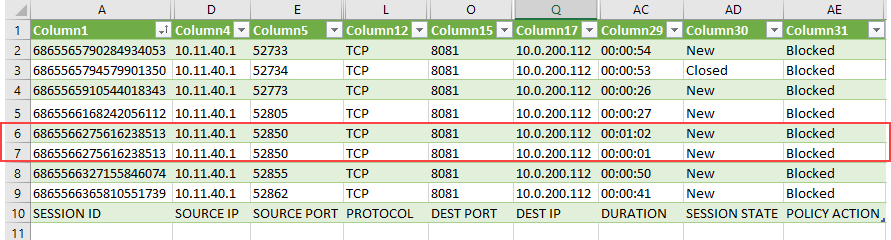
Xshield generates session IDs that are up to 19 digits. These session IDs are listed in the SESSION ID column on the CSV files that you download from Flow Explorer. With the default settings enabled, Microsoft Excel can only display a maximum of 15 digits in the cells. All additional digits are transformed to Zeros. See Last digits are changed to zeros when you type long numbers in cells of Excel for more details. The fixes listed in the Microsoft Excel documentation are only applicable when you type or copy more than 15 digits in the cells. These fixes do not work for the CSV files that you download from Flow Explorer. |
|
Workaround: To see the actual session IDs when they are more than 15 digits long, you must do the following:
|
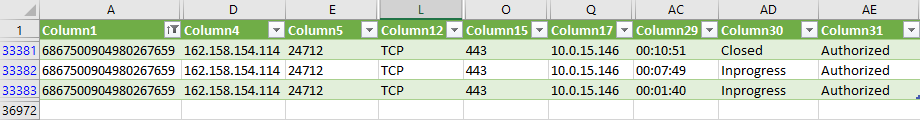
b. Long-lived sessions/flows are tracked as multiple rows in the CSV file
Sessions between assets or assets and unmanaged Internet and private entities can be short-lived or long-lived. Xshield tracks sessions by the 'Policy action' on the sessions - Unauthorized (Observe mode), Authorized (Observe, Enforce, or Encrypt mode), and Blocked (Enforce or Encrypt mode). The Xshield agents track the status of the sessions by using the following states - New (Xshield must receive more details about the session from the agent), In Progress (the session state was captured when the session was in progress), and Closed (the session was closed/terminated by the source asset/entity). The duration of the sessions are calculated based on the first and the last packet received in the session.
For long-lived sessions, the Xshield agents are designed to capture the state of a session at periodic intervals depending on the 'Policy action' on the session. So, for CSV files that contain the details of long-lived sessions, you will find multiple rows with the same session IDs.
|
|
Workaround: If you want to analyze the sessions by their session IDs, retain only the last session states of the sessions in the CSV file. Use Excel Macros to remove the rows with duplicate sessions IDs (the ones other than the row that displays the last state of the session). The data in the row that displays the last state of a session is the consolidated data for the session. |
For a short-lived session, you see only row in the CSV file.
Correlate connections data in the Visual Explorer fly panel with sessions log from Flow Explorer
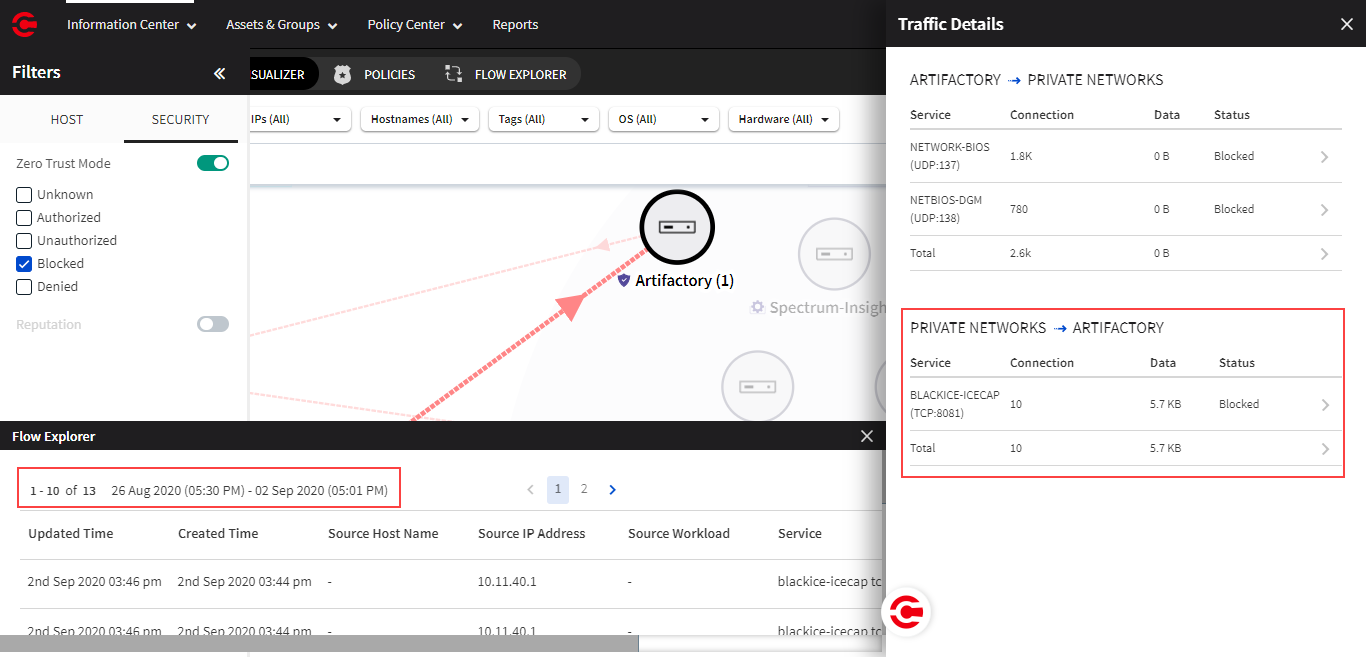
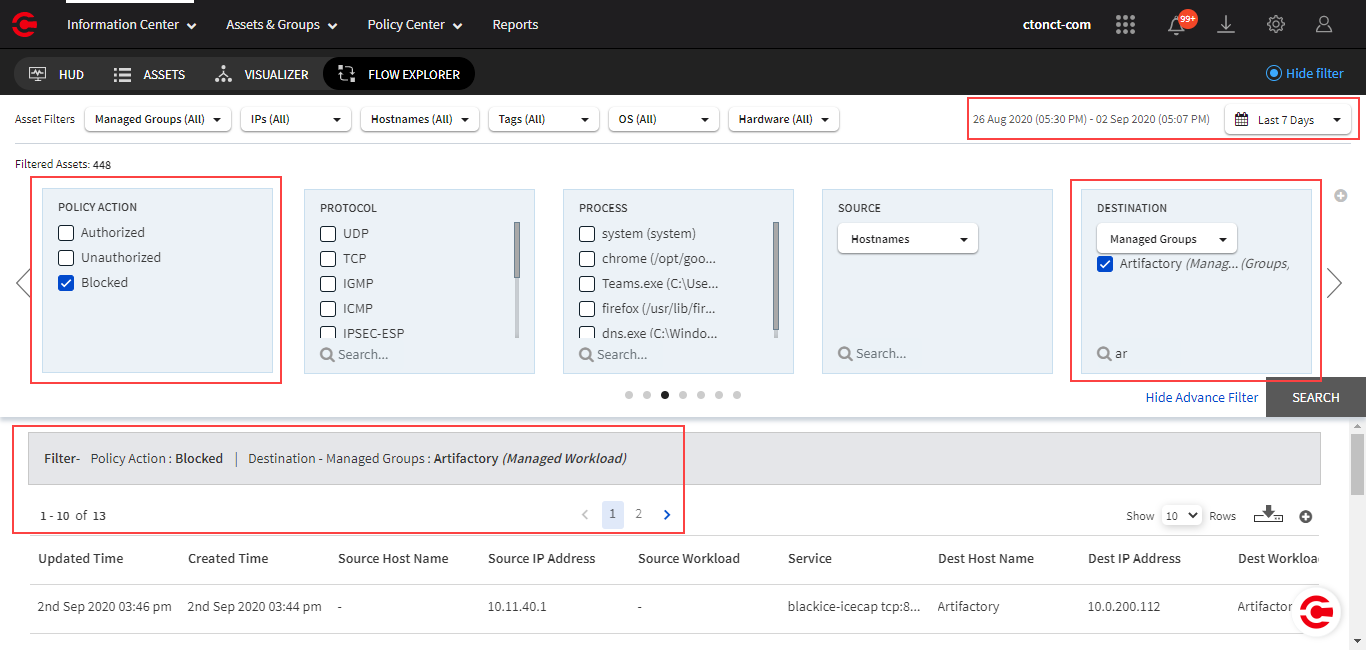
The connections data shown in the fly panel on Visual Explorer is the unique number of sessions (Unauthorized, Authorized, or Blocked). The related sessions log that you see and/or download from Flow Explorer is the sessions data for the related short-lived and long-lived sessions.
Visual Explorer fly panel
|
Flow Explorer
|
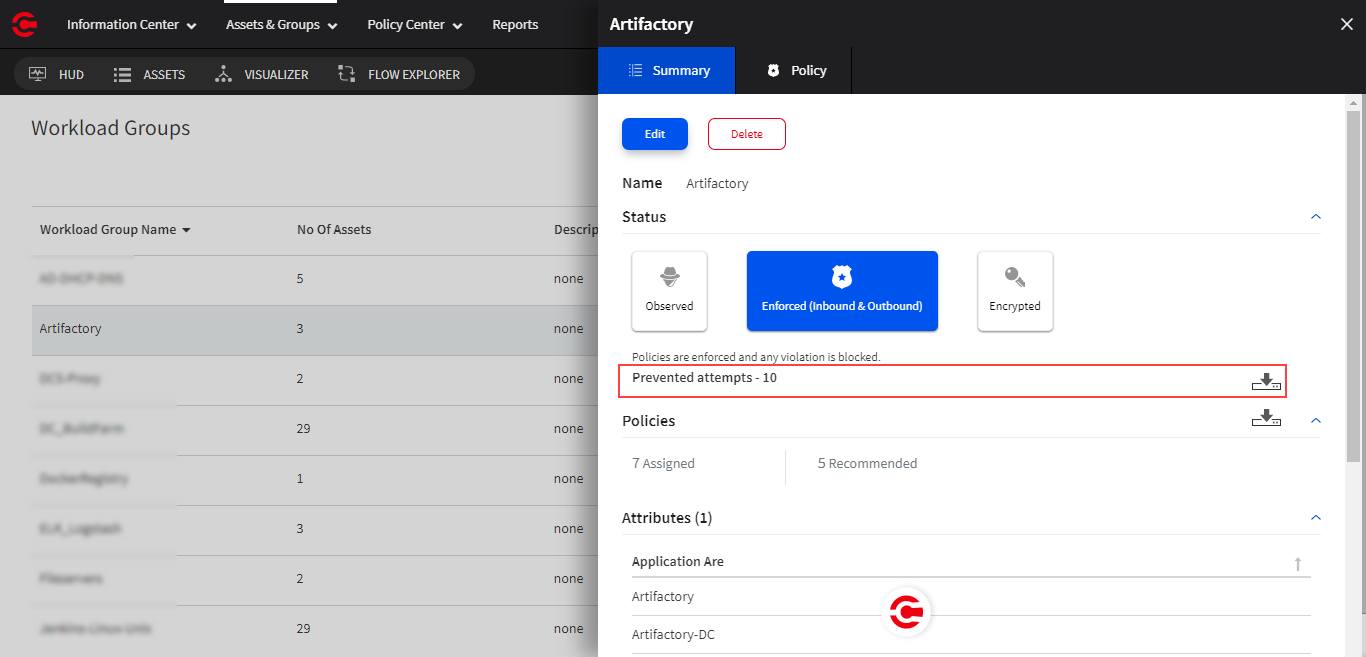
Correlate Unauthorized attempts and Prevented attempts in the Workload group fly panel with sessions log from Flow Explorer
The Unauthorized attempts detected and Prevented attempts count shown in the fly panel of a Workload group is the unique number of inbound sessions (Unauthorized or Blocked) in the last 7 days. The related sessions log that you see and/or download from Flow Explorer is the sessions data for the short-lived and long-lived sessions.
Workload group fly panel
|
Flow Explorer
|