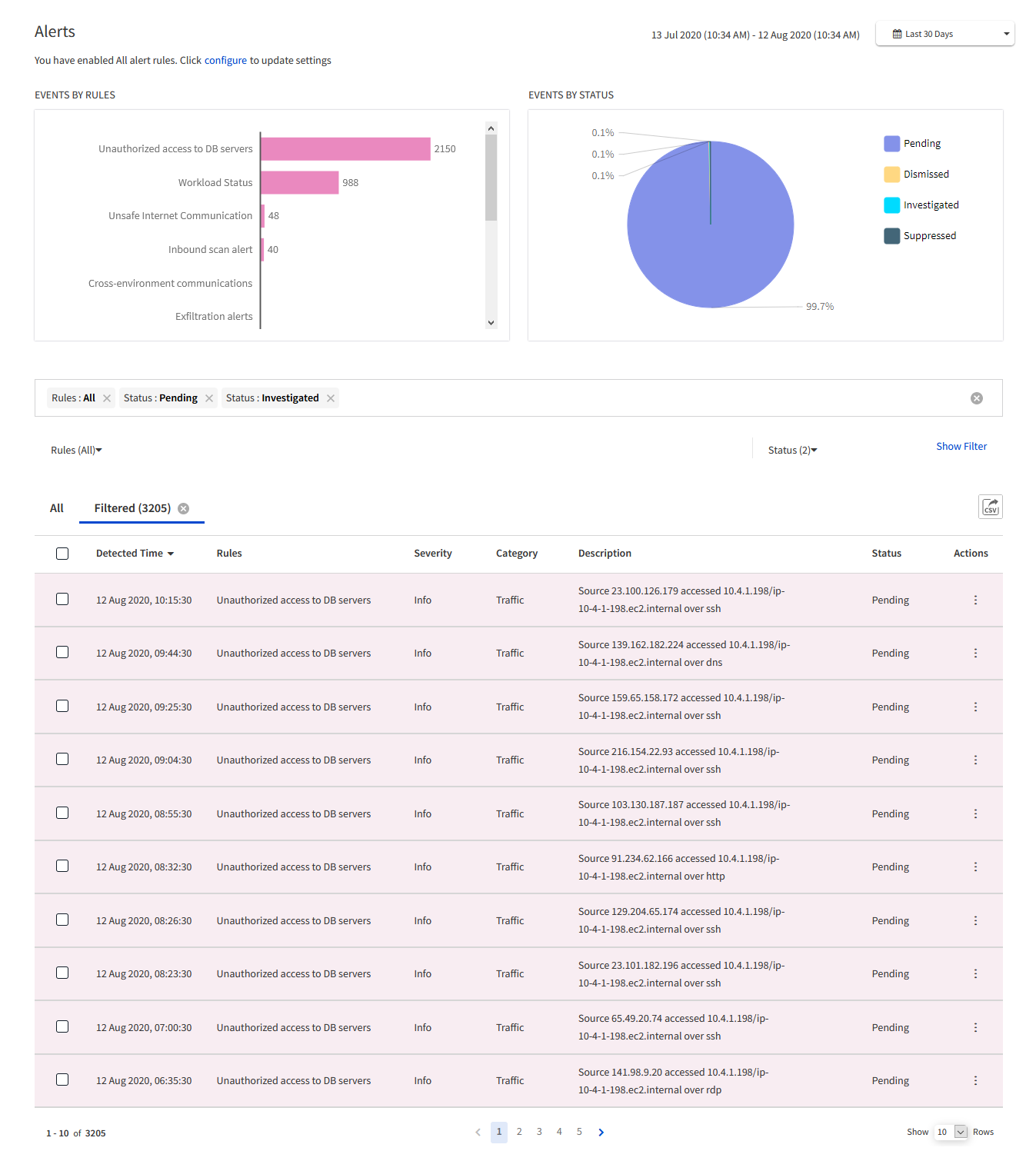
Alerts reported in Xshield
Xshield generates alerts for events such as unsafe perimeter traffic and anomalies and when the assets' reachability states change. The Xshield agents installed on the assets store the events as logs and send them to Xshield in real-time. All the event logs sent to Xshield from the assets include the details necessary to inspect and remediate the events. The details in the logs differ by type of event. You can see the alerts generated for the events on the Alerts page.
Although Xshield stores all the details of the alerts in its database, not all details are displayed on the Alerts page for brevity. For network traffic alerts, you must use Flow Explorer to view more details.
Alert categories and Severity levels
Xshield can generate up to 12 types of alerts. The alerts are categorized into Alert categories by the type of entity for which the alert is generated (Appliance, Asset, or Traffic). Alerts are also assigned various 'Severity' levels (by the severity of their impact on your network) - Critical, High, Medium, and Info.
See the following tables for the Alert categories and the associated alerts and Severity levels assigned to the alerts.
Appliance alerts
| Alert | Description | Severity level |
|
Appliance Deletion
|
Generated when appliances are deleted from the Settings > Configure > Appliances page | Info |
| Appliance Operational Status | Generated when appliances are disabled and enabled from the Settings > Configure > Appliances page | Info |
| Appliance Reachability Status
|
Generated when appliances are unable to connect with the Xshield instance (state=Offline on the Settings > Configure > Appliances page) and when they connect back with the Xshield instance (state=Online) | Critical (when appliances go to the Offline state)
Info (when appliances go to the Online state) |
| Appliance Software Upgrade
|
Generated when appliances are upgraded from the Settings > Configure > Appliances page | Info |
| Remote Access Connection
|
Generated when remote users connect to and disconnect from the Xshield-protected network (through Xaccess) | Info |
Asset alert
| Alert | Description | Severity |
|
Workload status
|
Generated when workloads are offline (state=offline) and when they are online again (state=online) |
Critical (when workloads are in the offline state)
Info (when the workloads are online again) |
Traffic alerts
| Alert | Description | Severity |
|
Cross-Environment Communications
|
Generated when assets in two different environments (based on the ENVIRONMENT tag in Xshield) communicate. For example, communication between workloads in the 'Staging' and 'Production' environment. | Medium |
| Exfiltration
|
Generated when the rolling average of data transferred over successive windows of 6 hours over a period of 7 days, from an asset to a public entity is more than 10 MB or twice the last rolling average
An alert is generated only at the first occurrence of a flow when an asset exceeds the data transfer limit to a unique public entity. |
Critical |
| Inbound Scan
|
Generated when a workload receives Five or more inbound connection requests on the blocked ports in the last one hour
If additional ports are scanned on a workload, the original alert will include the additional ports. Scans from public entities are titled 'Public inbound scan', and scans from private entities are titled 'Lateral inbound scan'. |
Critical
|
| Policy Violation
|
Generated when the Xshield policies enforced on a Workload group are violated.
An alert is generated only at the first occurrence of a unique policy-violating flow to the Workload group. Policy Violation alerts can also be sent as email notifications to the Org Admin and all the Instance Admins, Asset Managers, and Policy Managers of the instance. |
Medium
|
| Unsafe Internet Communication
|
Generated when there are inbound or outbound connections with Internet entities that pose a considerable threat to the network
An alert is generated only at the first occurrence of an unsafe flow for a unique combination of an asset and the asset's port, irrespective of whether traffic is from or to an Internet entity. |
Medium |
| Unauthorized Access to DB Servers
|
Generated when assets violate assigned or enforced policies and try to communicate with database workloads (ROLE tag = DB, in Xshield) | Info |
Enable/disable alerts
To reduce clutter on the Alerts page, only 'Critical' alerts are generated for a new Xshield instance. If you want to monitor alerts of other severity levels, you must enable them.
-
Alerts can be enabled or disabled at the level of an Alert category. For example, enabling the Traffic alerts category enables all applicable Traffic alerts (depending on the severity level you set for the Alert category).
-
Alerts can be enabled at the level of the severity of the alerts in an Alert category. For example, setting the severity level of the Traffic alerts category to Medium generates all Traffic alerts (Critical, High, and Medium) except Info-level Traffic alerts.
Alerts page
All alerts that are generated in the Xshield-protected network are listed on the Alerts page. The Alerts page displays the following widgets:
-
Events by rules - number of alerts generated for all types of Xshield alerts
-
Events by status - percentage distribution of alerts by their status (Pending, Dismissed, Suppressed, and Investigated)
All alerts are listed in a table with the following details - when the event occurred, the type of event/alert, the Severity level and Category of the alert, a description with the source and destination assets' details, and the current status of the alert. See Investigate alerts for more details about how to investigate and change the status of the alerts.
You can filter the Alerts page to see alerts only for the last 30 minutes, 1 hour, 24 hours, 7 days, or 30 days.
Integrate third-party Syslog tools
If you want to monitor and remediate alerts and audit logs generated for an Xshield instance, on/by using third-party Security Information and Event Management (SIEM) tools, you can integrate with a tool such as Splunk, Sumo Logic, or Kiwi Syslog Server. Alerts and audit logs are forwarded to the Syslog tool in the RFC 5424 format.
You can integrate only One third-party tool with an Xshield instance.
For third-party Syslog tool integrations, the Priority value of the alerts and audit logs sent are set a Facility value of 16 (local use 0 (local0)). The Severity levels of the alerts and audit logs translate to the following Priority values:
-
Critical - 130 (Severity value = 2)
-
High - 131 (Severity value = 3)
-
Low - 132 (Severity value = 4)
-
Info - 134 (Severity value = 6)
See Integrate third-party Syslog tools for more details.
Next steps
-
Enable more alerts or disable some alerts to suit your monitoring preferences.
-
Monitor alerts regularly and investigate and remediate security incidents, reachability issues, or performance issues. For operational ease and during experimental activities, you can temporarily suppress or dismiss alerts for selected assets.